Non Cryptographic Protocol Vulnerabilities - Obvious problems Interception of requests or compromise of DNS servers. The number of these devices is increasing rapidly which creates a massive and complex network with a vast amount of data communicated over that network.
Ajedigital Com
For most users the immediate risk is low but these vulnerabilities highlight that Telegram fell short of the cryptographic guarantees enjoyed by other widely deployed cryptographic protocols such as.

Non cryptographic protocol vulnerabilities. Basic DNS Vulnerabilities. Obviously the cryptohashing algorithm must not be a weak one when in doubt web security standards recommend AES 256 bits and up and RSA 2048 bits and up. A spoofing vulnerability exists in the way Windows CryptoAPI Crypt32dll validates ECC certificates.
Verifying Software Vulnerabilities in IoT Cryptographic Protocols. Non-cryptographically-secure pseudo-random number generators while providing uniform output are predictable rendering them useless in certain cryptographic scenarios. Cryptographic Hash Properties Applications Performance Birthday Attack Key Management Digital Certificates PKI Public Key Infrastructure Authentication One-Way Authentication.
Finally as we will show vulnerabilities in the 80211 MAC protocol allow an attacker to se-lectively or completely disrupt service to the network using relatively few packets and low power consump-tion. Used as basis for many security policies. This approach of lazily combining the reasoning power of a symbolic model checker and a cryptographic protocol verifier not only enables analysis of cellular protocols but can also be broadly applicable to analyze other real-world complex protocols.
A study of the T KIP cryptographic DoS attack ICON 2007. The focus of the case study is a protocol for online poker without a trusted third party also known as mental poker 41. And while it goes without saying that session IDs and sensitive data should not be traveling in the URLs and sensitive cookies should have the secure flag on this is very important.
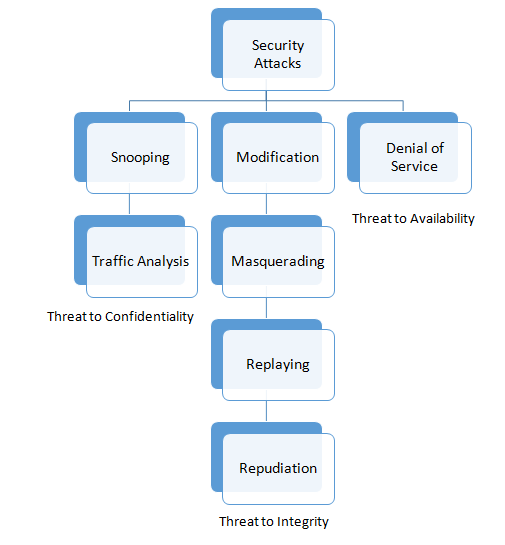
Non Cryptographic protocol Vulnerabilities What is denial of service attack. Exposing WPA2 security protocol vulnerabilities. There are many serious vulnerabilities in SSL and early TLS that left unaddressed put organizations at risk of being breached.
Discoverys new version discovers more hosts and more vulnerabilities and improves the visual representation of attacks. Leaving extra ISAKMPIKE and IPsec policies as acceptable policies creates a vulnerability to downgrade attacks. Browser same origin policy URL address bar.
Finding Security Vulnerabilities in IoT Cryptographic Protocol and Concurrent mplementations. Security Non-Cryptographic Protocol Vulnerabilities-DoS DDoS Session Hijacking and Spoofing Software Vulnerabilities- Phishing Buffer Overflow Format String Attacks SQL Injection Basics of Cryptography Symmetric Cipher Model Substitution Techniques Transportation Techniques. Non-cryptographic mechanism and has low com putational overheads.
Usershosts trust the host-address mapping provided by DNS. Attacker should not be able to do any of the following. The vulnerability of quantum coin-tossing and non-loophole-free Bell testing has previously been demonstrated 19 20 using imperfections in their specific experimental implementations to remove the protocols quantum advantages.
To the best of our knowledge this implementation is the largest program written in a security-typed language so far. Network Protocol Vulnerabilities Protocol Considerations for Security. Attacks in the Non-Access Stratum NAS layer procedures of 4G LTE network.
- learn the contents of messages between connecting parties - learn information enabling impersonation in a future exchange - learn anything that permits off-line password-guessing Impersonation of Originator. We achieve this by using a well-known visualization method called attack trees. The widespread POODLE and BEAST exploits are just a couple examples of how attackers have taken advantage of weaknesses in SSL and early TLS to compromise organizations.
Security services in the protocols as. Cryptographic protocols is described in Section 2. Include non-compliant cryptographic algorithms.
Blockchain is not as secure and unhackable as many people think. Internet of Things IoT is a system that consists of a large number of smart devices connected through a network. As a result of our analysis we found several cryptographic weaknesses in the protocol from technically trivial and easy to exploit to more advanced and of theoretical interest.
In Section 3 a short introduction to the notions of non-interference and admissible interference are given together with an unwinding theorem. We further compare our findings with non-cryptographic systems observing that these systems are indeed more complex than similar counterparts and that this excess complexity appears to produce significantly more vulnerabilities in cryptographic libraries than in non-cryptographic software. Blockchain ecosystems contain many vulnerabilities and are subject to many of the same scams frauds and hacks as other systems and some that are special to blockchain.
Ment and evaluate non-cryptographic countermea-sures that can be implemented in the firmware of existing MAC hardware. Cryptosense Discovery is our free tool to test a hosts usage of cryptography for common configuration mistakes and vulnerabilities. In downgrade attacks a malicious user or Man-in-the-Middle offers only obsolete cryptography suites and forces the VPN endpoints to negotiate non-compliant cryptography suites.
Our information flow method for the detection of potential resource exhaustion DoS is presented. According to Microsoft an attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable making it appear the file was from a trusted legitimate source. It is an attempt to make a machine or network resource unavailable to its intended users such as to temporarily or indefinitely interrupt or suspend services of a host connected to the Internet.
But there are civil remedies which could help recover stolen cyber currencies or those paid to resolve ransomeware attacks. Mentation of a non-trivial cryptographic protocol in the security-typed language Jif. In this Article we survey five quantum cryptographic primitives as examples to investigate practical security threats in their.
For most non-cryptographic applications there is only the requirement of uniform output of equal probability for each byte taken out of the pseudo-random number generator.

Public Key Cryptography Wikipedia

Pdf Non Cryptographic Authentication And Identification In Wireless Networks Security And Privacy In Emerging Wireless Networks

Pdf Non Cryptographic Authentication And Identification In Wireless Networks Security And Privacy In Emerging Wireless Networks
M2 Net Sec Pdf Denial Of Service Attack Transmission Control Protocol
Student Apamaravathi In
Introduction To Cryptography
Pdfcoffee Com

Jntuk R10 Cse 4 1 Syllabus

Pdf Finding Security Vulnerabilities In Iot Cryptographic Protocol And Concurrent Mplementations
M2 Net Sec Pdf Denial Of Service Attack Transmission Control Protocol

Pdf A Survey Of Cryptographic And Non Cryptographic Techniques For Privacy Preservation

Cs M S022 Non Cryptographic Protocol Vulnerabilities Youtube

Doc Cns Unit Tejaswini Jogi Academia Edu

Overview Of Cryptographic Protocol Development Download Scientific Diagram
